Microsoft has some great Quickstart templates for deploying resources as codes. For this post I've looked at deploying an Azure Firewall into multiple availability zones using Bicep.
The Quickstart guide used can be found here.
The template needs only a few changes. I updated the VNet name and IP address info and inserted a reference to a key vault for the VM admin password.
My updated files can be found on Github (fw-conn-weu-001.bicep and fw-conn-weu-001.parameters.json).
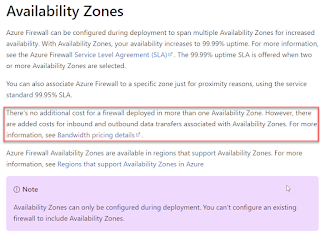
The firewall is deployed into three availability zones in West Europe. This increases the availability to 99.99%. There is still only one logical firewall deployed, so the increased availability is managed in the background by Microsoft. And from a Azure Portal point of view it looks the same as if only deploying to one availability zone.
The availability zones can be verified under Azure Firewall -> Properties, see below:










No comments:
Post a Comment
Note: Only a member of this blog may post a comment.