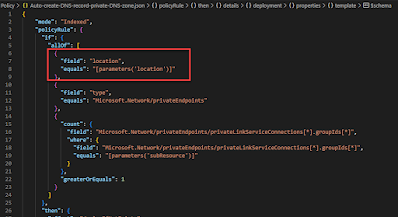
As part of the Azure Landing Zone architecture, there is a policy that denies the creation of VNet peerings to non-allowed VNets, see policy here.
This policy is relevant to a apply in a hub-spoke setup where you want to avoid that spoke VNets, or spoke landing zones, can create VNet peerings to anything other than the defined Hub VNets.
At current client we've been running this policy since December, 2023 and it's been working fine.
However, about a month ago some policy evaluation behavior changed (the policy itself or the templates have not changed) and now for certain bicep files, the policy blocks deployments even when using approved VNets for the peering. It wasn't for all bicep files and ARM templates still worked.
Microsoft Support came up with a minor update to the policy definition to effectively have the same rule but the syntax is slightly different. This works.
We haven't found an explanation yet as to why there was a change in policy evaluation behavior.
But the updated policy can be found here on Github.